ICE's WHITE PAPERS

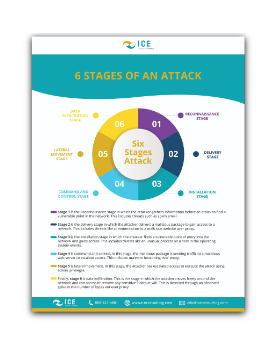
6 Stages of a Cyber Attack
Contrary to popular belief, cyber attacks do not occur rapidly; instead, hackers gain access and methodically navigate through the system. This deliberate approach makes them challenging to detect. Access our flier to discover the 6 stages of a cyber attack. Understanding these phases will empower you to recognize their tactics and proactively detect any attempt to infiltrate your system.
Download
Cybersecurity 101
Cybersecurity has gained significant attention, especially with a fivefold increase in data breaches in 2020. While many business owners recognize the issue, they often get stuck in analysis paralysis, unsure of how to begin. Our cybersecurity 101 flyer offers valuable insights to help you learn how to evaluate your security posture, and discover a strategy that is best for you.
Download
Managing Risk in IT
The life sciences sector heavily depends on data, with companies closely monitoring experiments for even minor result changes. IT is crucial for their success, as any threat to their infrastructure is extremely risky. A device malfunction or software update failure could stop operations at a research facility until fixed. Check out our guide to navigate these high-stakes environments effectively.
Download
What is a Zero Trust Model
The zero trust security model, also known as zero trust architecture or perimeter less security, provides a holistic approach to IT system planning, design, and execution. In today’s changing landscape, this strategy effectively protects organizations. This guide outlines the advantages of implementing ZTNA for enhanced security and peace of mind.
Download
SOC as a Service Made Simple
Setting up a Security Operations Center involves detailed steps, with a variety of benefits. A Security Operation Center as a Service (SOCaaS) can shift your security strategy from reactive to proactive. Regardless of how many security solutions you have in place, over 90% of data breaches are the result of human error, therefore going on the offensive is so important.
Download
Managed IT Services are too expensive?
Myth Buster: Throughout the past 26 years, we have collaborated with numerous companies, aiding them in achieving average savings of over 25%. By partnering with an IT Provider, the necessity to budget for daily tasks is eliminated. They handle software, upgrades, support, service, and 24/7 monitoring. Download the paper to learn more.
Download
Working with a SOC 2 Certified Vendor
The SOC 2 certification is a prized achievement in information security. It shows that an external firm has rigorously tested an organization's non-financial reporting controls to ensure secure operation. Discover its significance in our white paper.
Download
Security Operation Center as a Service
If your company's strategy is reactive rather than proactive, you're at risk of cyber threats. With cybercrime increasing, a 24/7 security operation is vital for protection. Download our flyer for the cost breakdown of setting up this security measure internally.
Download
Essential Tool Kit for Remote Workers
Remote work is becoming permanent. Soon, most employees may work remotely. This change improves work-life balance but also leads to increased cybercrime. Check out our guide to learn more on remote work vulnerabilities.
DownloadClick the button to learn more about our Managed IT Services
Any IT or Cybersecurity Questions?
Connect with our cybersecurity professionals today for a free consultation